Vajra- Endpoint Detection and Response Tool
Prof. Manjesh Hanawal
An integrated endpoint security solution that combines real-time monitoring and analysis of endpoint data with automated response and remediation capabilities.
1. Cybersecurity Auditing Tool:
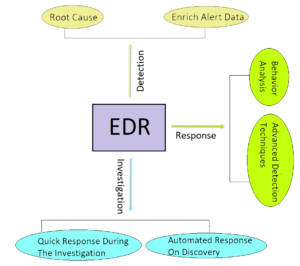
We have developed an Endpoint Detection and Response (EDR) for linux systems using open-sourced tools like Osquery, Fleet server and Elastic. The advantage of building an in-house EDR tools against using commercial EDR tools provides both the knowledge and the technical capability to detect and investigate security incidents. In our method all the endpoint logs are collected at a common server which we leverage to perform correlation between events happening on different endpoints and automatically detect threats like pivoting and lateral movements.
2. Vulnerability Assessment and Exploit Generation:
Vulnerabilities of applications expose them to attacks. However, identifying the vulnerabilities could be tedious and time-consuming. Our first goal of the project is to automate the process of identifying vulnerabilities in applications. We propose to develop a fuzzing based methodology to automatically identify the vulnerability. Specifically, this task will involve fuzzing and symbolic execution based on binary complexity to automatically detect vulnerabilities.
-Machine learning-based Smart Fuzzing
-Development of an automated tool to analyze the vulnerabilities
-Testing of functionalities of the tool on various standalone applications
Our second goal is to automate/semi-automate the process of exploit generation once the vulnerabilities are identified. Manual exploit generation requires a developer to be aware of a number of details such as location of control flow critical data like return address, the size of the stack, and precise semantics of each instruction. We propose to automate this process of exploit generation.
Our third goal is to automate the process of firmware extraction and automating it’s reverse engineering for applications/ firmware pertaining to mobile devices/ SDRs. The firmware extraction process is to understand the device architecture and access the device firmware in a readable format. Firmware reverse engineering is to identify the functionalities of the device from the extracted firmware. Further identify the vulnerabilities present in the device incorporating different methods.
Key Highlights:
Key Features:
